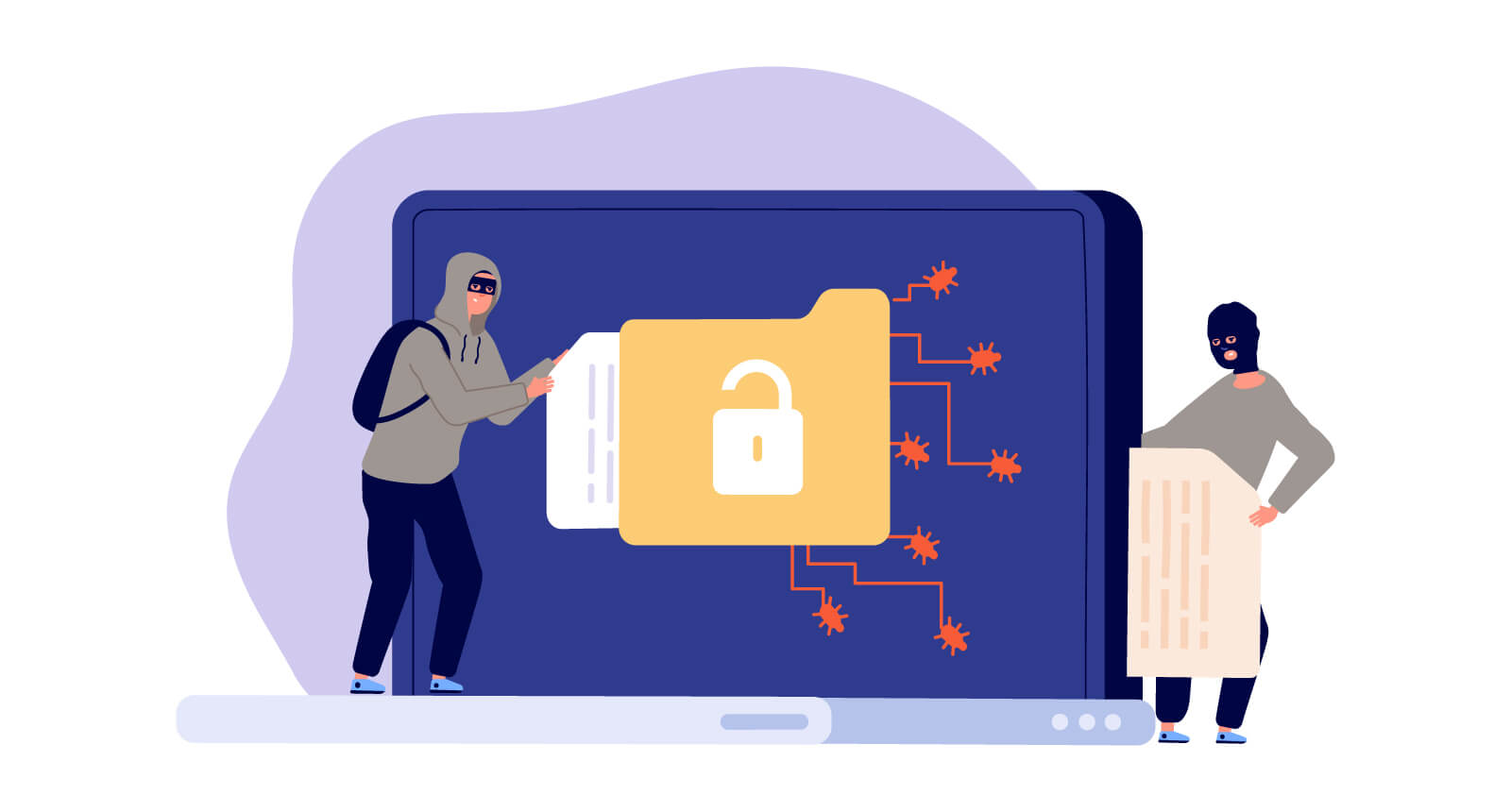
Spoofing is a well-known cyberattack that happens when scammer disguises themselves as a trusted source to access essential data or information of their target. Spoofing can occur anytime through websites, emails, phone calls, texts, IP addresses, and servers.
Usually, the purpose of spoofing is to obtain confidential, personal information, steal money, bypass network access controls, or spread destructive malware through infected attachments or links. Scammers try to use spoofing to steal your identity and assets through communicating online. This blog will tell you about how spoofing happens and how you can prevent spoofing attacks by following some best practices.
How Does Spoofing Happen
The term "spoof" dates back to centuries ago. It is associated with some forms of trickery. However, as things evolved, people started incorporating several illegal and tricky activities in the digital world to attack people. Soon this activity became a cybercrime. Any time a scammer disguises their identity as another to attack you for confidential information or ransom etc., it's spoofing.
Spoofing can happen through several communication channels and engage different levels of technical know-how. To conduct a successful spoofing attack, the attackers use a certain level of social engineering. Scammers' methods can trick their victims into giving out their personal information as if they are talking to the correct person. Scammers are highly polished in using social engineering to play on vulnerable human characteristics, such as greed, fear, and naiveté, which let them win in their plans. Cybercriminals use strategic social engineering methods to persuade victims to click links, download attachments, fill out web forms, and respond to text messages.
How To Prevent Spoofing

Stay Focused
Always remain observant against the most common types of spoofing attacks. Look out for common signs related to it, and you'll have a much lower chance of getting fooled.
Call to confirm
If someone asks you to submit any personal information, like a password, financial data, or credit card number, call the sender to confirm. You might call on the contact number listed on the spoofing source. Never use that. Use the contact number listed on their real, actual website. Manually enter their URL into your web browser, check the padlock sign for security, and never click on any link attached to any suspicious email you received.
Beware of strange attachments
Don't open random attachments that you don't expect to receive or when you don't know the sender, and especially when they have unusual file extensions.
Hide your IP address
Contact your IT team and learn how you can hide your IP address. Get in the habit of hiding you IP when surfing the web to prevent IP spoofing.
Periodically change your passwords
If the attacker anyhow manages to capture your login credentials, they won't be able to access anything if you regularly update it with a new password. Create strong passwords that are difficult to guess and use a password manager to store them securely.
Check links before you click
To verify the URL, you must hover over links before you click. If you click, always confirm the URL after the page loads to ensure you weren't redirected. Stick to sites that have a padlock sign next to their URL, which is HTTPS encrypted.
Report spoofing attempts immediately
If you get any spoofed email or other communication, let the supposed sender know that they've been spoofed. This can help stop future spoofing attacks.
Educate your team
You must switch to a browser that prioritizes safety and privacy and one that's less exposed to hijacking attempts than normal browsers.
Use a secured browser
You can use GlobalSign Secure Email Solutions to counter phishing and data loss. When deployed, it clearly presents the sender's identity to the recipient to help differentiate it from spoofed emails. It encrypts every single email to protect contents in transit and at rest.
Use email protection services
Focus on educating your team about social engineering, spoofing, and other types of cybercrimes. Educate your organization on how these malpractices happen. Conduct training to show how easy it is to be tricked. You can also contact us to get detailed information about real-world scenarios.Spoofing attacks can happen to anyone. Thankfully, GlobalSign Secure Email Services includes multiple advanced features that work together to provide real-time spoofing protection. With us by your side, you'll be protected against all kinds of online attacks that criminals love to create.