Secure Sockets Layer (SSL) was the most widely deployed cryptographic protocol to provide security over internet communications before it was succeeded by TLS (Transport Layer Security) in 1999. Despite the deprecation of the SSL protocol and the adoption of TLS in its place, most people still refer to this type of technology as ‘SSL’.
SSL provides a secure channel between two machines or devices operating over the internet or an internal network. One common example is when SSL is used to secure communication between a web browser and a web server. This turns a website's address from HTTP to HTTPS, the ‘S’ standing for ‘secure’.
HTTP is insecure and is subject to eavesdropping attacks because the data being transferred from the web browser to the web server or between other endpoints, is transmitted in plaintext. This means attackers can intercept and view sensitive data, such as credit card details and account logins. When data is sent or posted through a browser using HTTPS, SSL ensures that such information is encrypted and secure from interception.
How Do I Know a Website is Secure with SSL?
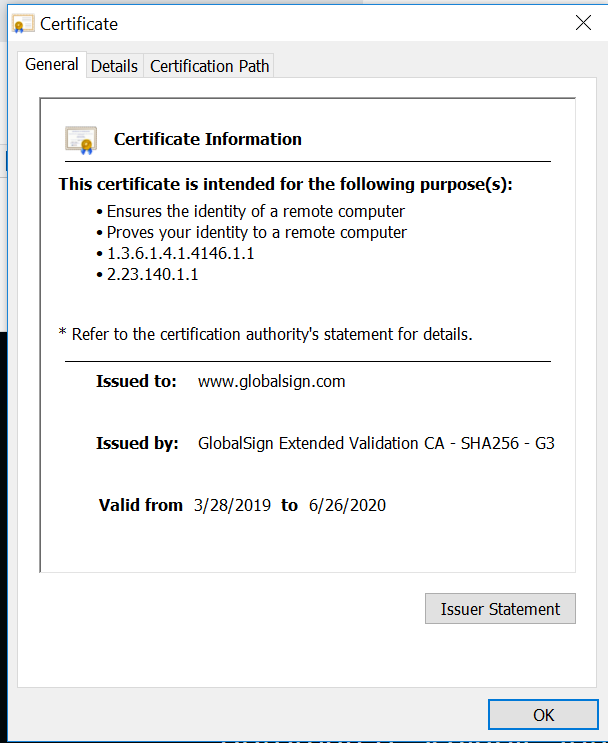
Technically, SSL is a transparent protocol which requires little interaction from the end user when establishing a secure session. In the case of a browser, you can tell if a site is using SSL when a padlock is displayed and you click on the padlock to reveal the digital certificate information.
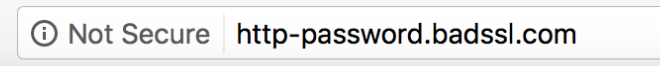
Here is an example of a website secured with SSL in Chrome 81 versus a website that is insecure.
Using SSL

Not Using SSL
Why Do I Need SSL?
With so much of our day to day transactions and communications happening online, there is very little reason for not using SSL. SSL supports the following information security principles:
- Encryption: protect data transmissions (e.g. browser to server, server to server, application to server, etc.)
- Authentication: ensure the server you’re connected to is actually the correct server
- Data integrity: ensure that the data that is requested or submitted is what is actually delivered.
SSL can be used to secure:
- Online credit card transactions or other online payments.
- Intranet-based traffic, such as internal networks, file sharing, extranets and database connections.
- Webmail servers like Outlook Web Access, Exchange and Office Communications Server.
- The connection between an email client such as Microsoft Outlook and an email server such as Microsoft Exchange.
- The transfer of files over HTTPS and FTP(s) services, such as website owners updating new pages to their websites or transferring large files.
- System logins to applications and control panels like Parallels, cPanel and others.
- Workflow and virtualization applications like Citrix Delivery Platforms or cloud-based computing platforms.
- Hosting control panel logins and activity like Parallels, cPanel and others.
How Do I Get SSL?
To adopt SSL in your business, you should purchase an SSL Certificate.


