Within DevOps, Kubernetes has become the de-facto orchestration tool for containers, allowing organizations to efficiently deploy and manage their applications. According to CNCF’s respondents, 96% of organizations are either using or evaluating Kubernetes – a record high since their surveys began in 2016. With this increasing adoption, ensuring the security of Kubernetes deployments is paramount. Ingress Controllers play a crucial role in routing external traffic to services within a cluster. Securing these Ingress Controllers with TLS certificates is essential for protecting the confidentiality and integrity of data transmitted over networks.
Kubernetes Ingress Controllers need TLS certificates to remain secure and help keep your development cycle safe. Through GlobalSign’s Atlas issuer for cert-manager and ACME service, you can maintain security in your Kubernetes Ingresses and keep your information secure.
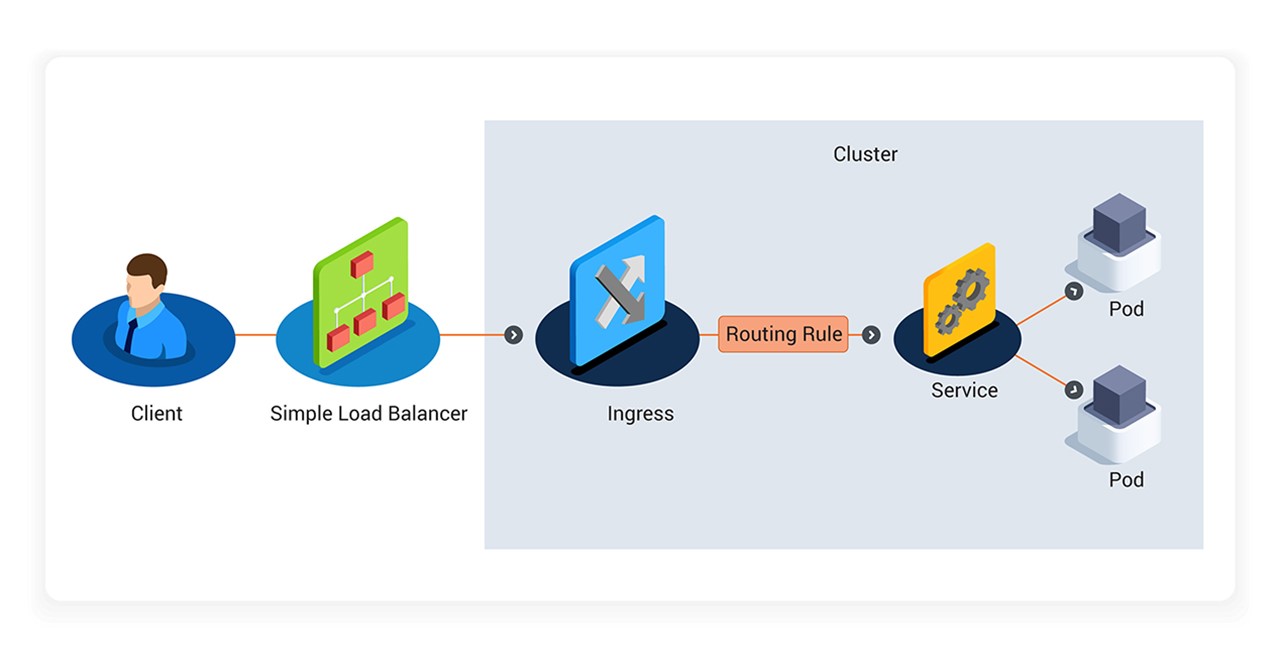
The Kubernetes Ingress Routing Policy governs how users can route external traffic to services within clusters. Via a simple load balancer, a client can implement the routing rules to configure the infrastructure which has been defined in the cluster to be routed to services accordingly.
Why You Should Be Securing Ingress Controllers with SSL / TLS Certificates
- Encrypted Communication: TLS certificates provide encryption, ensuring that data transmitted between clients and the Ingress Controllers remains confidential. This prevents man-in-the-middle attacks, and mitigates the risk of sensitive information being intercepted or compromised.
- Data Integrity: TLS certificates enable integrity checks, protecting against tampering and cyber-attacks, and ensuring that data remains secure during transit. By verifying the authenticity and integrity of the communication, organizations can trust the data being exchanged between clients and services.
- Authentication: Certificates enable client and server authentication, establishing trust and prevents unauthorized access to the Kubernetes cluster. This mitigates the risk of malicious entities intercepting or modifying data.
- Compliance Requirements: Industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR), mandate the use of TLS certificates to protect sensitive data. Securing Ingress Controllers with digital certificates enables organizations to meet these compliance requirements.
Many developers do use self-signed TLS certificates for development or testing environments. These are generated by using opensource tools like OpenSSL, however as they are not signed by a trusted Certificate Authority (CA), they are not fully compliant and could pose risks to your environment.
Learn more about the risks associated with self-signed certificates
How GlobalSign’s Digital Identity Platform, Atlas, Secures Kubernetes Ingress Controllers
As a publicly trusted CA, GlobalSign recommends the use of compliant digital certificates for development, testing and production environments. GlobalSign offers three different solutions to secure your Kubernetes Ingress Controllers using Atlas.
- Atlas Issuer for cert-manager: GlobalSign’s Atlas plugin for cert-manager allows users to access Atlas APIs from the GitHub repository to simplify certificate issuance requirements in Kubernetes. This Issuer allows developers to obtain trusted TLS certificates for Kubernetes resources to secure Kubernetes Clusters.
- Atlas – HashiCorp Vault Plugin: Use GlobalSign’s HashiCorp Vault integration for hassle free digital certificate issuance. The plugin manages and secures all API keys and secrets.
- Atlas-ACME Service: Using the ACME protocol (using either HTTP or DNS validation), Atlas issues fast and scalable digital certificates for your DevOps environment.
Automating DevSecOps pipelines with plug-ins and integrations helps to alleviate the burden of manual intervention in DevSecOps pipeline security. The ongoing shift left in DevOps environments is founded on sewn-in security throughout the pipeline, but this can place additional time constraints and heavier workloads on DevSecOps teams. Automation helps to streamline these processes and prevent the overburdening of DevSecOps teams while keeping up to date with regulations and improving pipeline security.
Ensuring Robust Security for Kubernetes Ingress Controllers
As Kubernetes continues to dominate container orchestration, securing Kubernetes Ingress Controllers with TLS certificates is not just a best practice but a necessity in today’s DevOps environments. GlobalSign’s Atlas issuer for cert-manager, along with its other integrations, provides a robust framework for automating and securing your Kubernetes Ingress Controllers. By leveraging these tools, organizations can streamline their DevSecOps pipelines and maintain a high level of security across their development, testing, and production environments. Embracing these practices will not only safeguard your data but also enhance the overall reliability and trustworthiness of your Kubernetes deployments.







