As more Enterprises are adopting a DevOps culture it is clear that container adoption overtakes the maturity of cloud-based practices. According to the latest CNCF Survey, 44% of respondents are already using containers for almost all applications and business segments, 35% are using containers across some production applications within their organisation, whilst 9% are in early adoption stage where they are piloting or actively evaluating container use.
The Adoption of Docker Containers
Docker containers have revolutionized the way developers create, deploy, and manage applications. They have become increasingly popular as they offer a lightweight and portable solution for building, testing, and shipping software. However, just like any other software, Docker containers are vulnerable to attacks. One of the most effective ways to secure Docker containers is using SSL/TLS certificates.
In this blog, we will explore why it’s important to secure Docker containers using SSL/TLS certificates, and how to do it.
SSL/TLS certificates are widely used to encrypt the data flow across private and public networks. In the case of Docker containers, SSL/TLS certificates can secure the following:
-
Communication between the Docker daemon and the client
-
Communication between Docker containers
-
Communication between Docker hosts
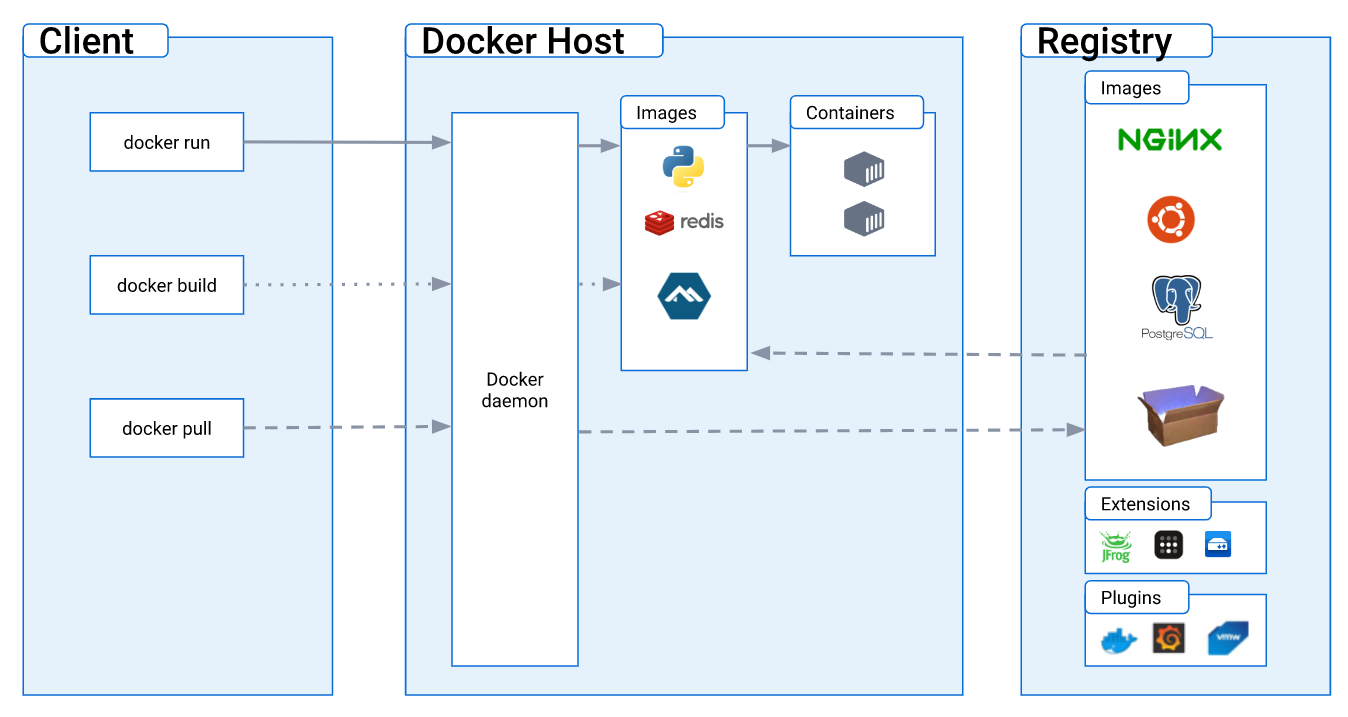
Docker host architecture. Image Source: docs.docker.com
Securing Communication Between Docker Daemon and Client Using TLS Certificates
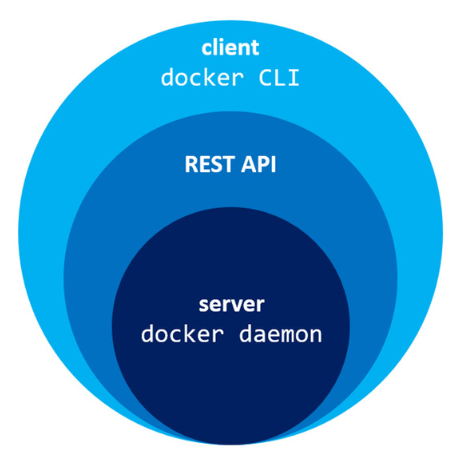
Visualizing Docker’s Architecture. Image: nickjanetakis.com
The Docker daemon is responsible for managing Docker containers and images. It uses a network socket to detect Docker client requests. When a Docker client sends a request to daemon, it must authenticate itself to ensure that it is authorized to perform the requested operation. SSL/TLS certificates are used to securely authenticate the Docker client to daemon, ensuring that only authorized clients can access the Docker daemon.
Securing Communication Between Docker Hosts
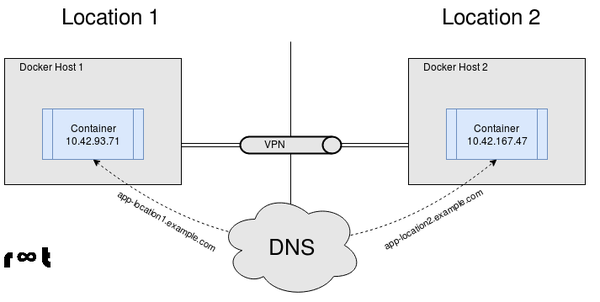
In a Docker swarm or Kubernetes cluster, multiple Docker hosts work together to run and manage containers. When these hosts communicate with each other, it is crucial to ensure that the communication is secure. SSL/TLS certificates are used to encrypt and authenticate communication between Docker hosts.
4 Steps to Securing Communication Between Docker Containers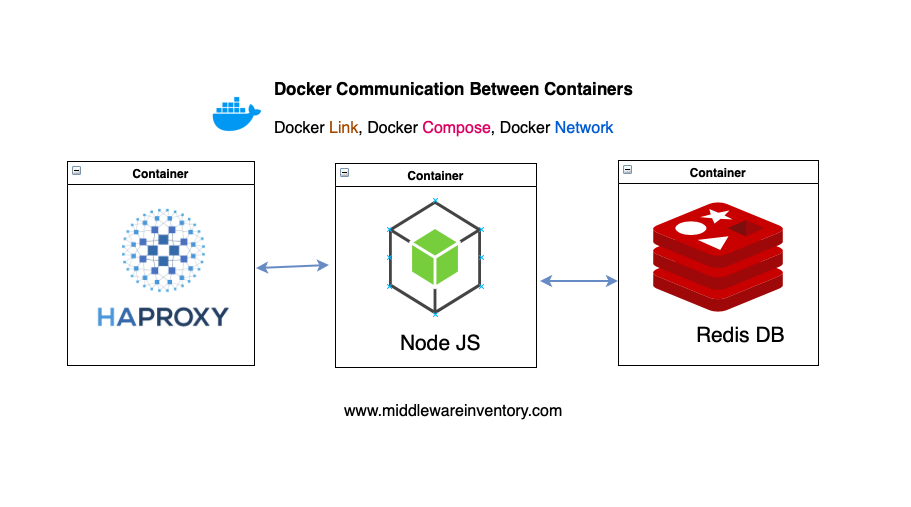

Image source: middlewareinventory.com
When multiple Docker containers run on the same host, they may need to communicate with each other. This communication can be vulnerable to ‘man-in-the-middle’ attacks if data is not encrypted and authenticated. SSL/TLS certificates can secure Docker containers and allow them to communicate with each other, ensuring the communication is encrypted and authenticated.
Now that we understand the main use cases for securing Docker communication, we will explore how to secure Docker containers using SSL/TLS certificates.
Step 1: Use Private or Public Certificates from a Trusted Certificate Authority (CA)
A CA is responsible for issuing SSL/TLS certificates that will be used to secure communication between Docker hosts, containers, and clients. Developers can sometimes be inclined to use self-signed certificates but this poses a potential threat to your infrastructure as these self-signed certificates are not publicly trusted, or compliant. We always recommend securing your infrastructure with certificates from a CA, such as GlobalSign.
Step 2: Generate Certificates and Secure your Secrets
Not only do you need certificates to secure your infrastructure, you also need to ensure that your certificates and private keys are stored securely. GlobalSign’s Hashicorp Vault – Atlas Plugin helps enterprises secure Docker Containers by obtaining SSL/TLS certificates from Atlas, and managing secret storage by securely storing them in the Vault. This enables enterprises to focus on application development and leave the security to us.
Step 3: Configure Docker to use TLS Certificates
Once your certificates have been generated, Docker will need to configure these for use. This requires configuring the Docker daemon to listen on a SSL/TLS enabled socket to configure the Docker client to use the SSL/TLS certificate to communicate with daemon. Your container will then need to be configured to use the SSL/TLS certificates, using configuration files or environment variables.
Step 4: Verify that the TLS Certificate is working
After configuration, it is essential to verify that the SSL/TLS certificate is working correctly. This can be done by testing the communication between Docker hosts, containers and clients to ensure that it is encrypted and authenticated.
Containers are more likely to be exposed to malicious attacks than virtual machines because of their architecture, so it is recommended for enterprises to secure their containers and orchestration environments (like Kubernetes), with SSL/TLS certificates. As a renowned Public Trusted Certificate Authority, GlobalSign can help enterprises secure their DevOps infrastructure.







