Most small business enterprises believe that attackers only target large-scale brands and hence do not consider investing in their website security.
In reality, SBEs' websites are at equal risk of being attacked. They are specifically vulnerable because they don't have the resources to resolve such issues promptly.
In fact, several news reports affirm the rate of cyber attacks on small business enterprises' websites is increasing. Attackers are stealing and misusing sensitive users' data and business financial information. This can harm a brand's reputation and impact its bottom line.
So, how can brands ensure complete website security? What are the security measures they need to take to protect their websites from such attacks?
In this post, we will share six actionable tips for SBEs to protect their websites from attackers.
1. Protect Your Business Website Against SQL Injection
SQL Injection (SQLi) is a malicious code-based vulnerability that enables attackers to access, read, and manipulate sensitive data from the database.
A successful SQLi attack can result in unauthorized viewing of your customer lists and deletion of information. In some instances, the attacker may gain administrative rights to the database.
Small business enterprise websites that use SQL databases, such as Oracle, MySQL, SQL Server, and others, are at serious risk of SQL injection attacks.
Here's a recent case of SQLi attack.
In July 2021, a group called REvil attacked around 1500 businesses managed by Kaseya, an IT software provider firm. The hackers exploited the SQL vulnerability of their servers by executing a command that deployed malicious updates.
Here are a few tips to prevent your website against SQLi attacks:
-
Perform Frequent Scans: Scan your website consistently to identify, assess, and resolve vulnerabilities. Count on automated vulnerability scanning tools, such as OpenVAS and OpenSCAP, to perform scans.
-
Restrict Privileges: Limit user permissions and access to the database and its components. This can make it difficult for attackers to access your sensitive data.
-
Include Parameterized Query: This allows businesses to place parameters in an SQL query rather than a constant value.
See the following query.
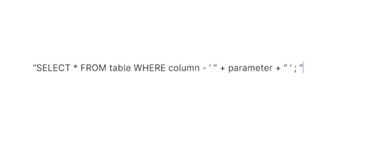
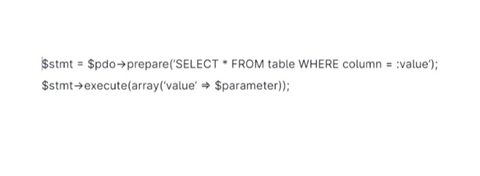
2. Shield Against XSS Attacks
Also called cross-site scripting, XSS attacks occur when cybercriminals inject malicious scripts into trusted websites. The attackers usually use a web application to inject malicious codes (browser-side script form).
A successful XSS attack happens when data enters a web application via an untrusted web request without validation.
Website cookies, search fields, forums, and comments are a few most vulnerable areas to XSS attacks. For instance, by injecting malicious code, cybercriminals can gather your website cookie data and steal user information, such as their login information, debit/credit card number, session IDs, and more.
Here are a few tips to protect your website from the XSS attack:
-
Validate User Input: Treat data from external sources as untrusted and verify it every time.
-
Sanitize the Data: Eliminate unwanted data, such as HTML tags, that might be unsafe for the website.
-
Ask for Passwords: Ask users to re-enter passwords before accessing crucial pages on your business website (despite information in the cookies).
Pro Tip: Use an advanced security development lifecycle to limit the coding errors during the website application development. This can help protect your business website from XSS attacks.
3. Keep a Tab on File Uploads
Enabling users to upload files without verification can make your website vulnerable to threats.
Even a simple image upload permission without proper validation of aspects, such as file name, content, type, or size, can put your database at high risk of getting hacked.
The file can comprise server-side script files that allow attackers to execute remote code and damage the entire database.
Here's what you can do:
-
If your website has a form that allows file uploads, verify each file to protect it from malicious code.
The best measure to take here is to stop direct access to uploaded files. This will ensure that the uploaded files get stored in a separate folder. Create a script to identify and verify those files before delivering them to your browser. -
If your website allows uploaded files, use secure transport methods like SFTP (Secure File Transfer Protocol) for complete data security.
-
If you use cloud hosting, you can permit or deny file uploads based on user location (IP address). For instance, you can block uploads from countries like the US and China while allowing other geo-locations.
4. Tighten Network Security
Employees in your team may create an unsafe environment for the website. For instance, they may inadvertently allow unauthorized access to the website server by updating software from a malicious link.
Hence, it's pivotal that you analyze and tighten network security.
Here are a few tips to consider:
-
Get a web application firewall (WAF) to protect your team against attacks that target website applications.
-
Lock IP (internet protocol) addresses to prevent your network from attackers.
-
By default, most small business enterprise routers use dynamic host configuration protocol (DHCP), which automatically provides IP addresses to systems in the network. However, if the network is exploited, attackers may access your systems. In such instances, locking down IP addresses can help.
-
Scan all the plugged devices into the network for malware each time your team uses them.
-
Have computer logins expire within an hour or two of inactivity. Besides, ensure that your team's system notifies them of password changes every few months.
Pro Tip: Educate your team about network security and its significance. Train them to keep a tab on necessary measures to maintain the website's data security.
5. Create a Backup of Your Website
Regular backups can help recover your website information after a serious security incident. The backups should contain all the files, emails, customer information, and the entire database.
Remember that failure to back up the data will lead you to rebuild the website from scratch. This could take several months and impact your branding, search engine optimization rankings (SEO), and sales.
However, avoid storing the backups on your website server because attackers can damage it again.
What's the best solution?
Store the data in the cloud with strong password protection. It will allow you to recover and access vital information at any instant in a secure manner.
Pro Tip: Count on tools like Handy Backup and Comodo to streamline and schedule your website backup process. These software solutions have robust and reliable data recovery systems that can help you recover crucial files at any point.
6. Pay Attention to Email Transmission Ports
Attackers often target business emails to gain access to sensitive website information.
A report revealed that enterprise email is the top threat vector for cyber attacks. In 2022, 94% of US-based firms experienced impersonation or spear phishing attacks.
So, ensure that all email transmissions are secure to prevent your business website.
Here's a simple way to identify it -
Visit your business email settings and check out the communication ports.
-
Email communications through the following ports are secured via encryption.
-
IMAP Port 993
-
POP3 Port 995
-
SMTP Port 465
-
The following ports are not secure.
-
POP3 Port 110
-
IMAP Port 143
-
SMTP Port 25 ports
Switch to secure communication ports to avoid data breaches.
Summing Up
A cybersecurity attack can be detrimental and impact your enterprise's reputation and revenue in the long term. If you don't invest in website security measures because of a tight budget, you may need to rebuild your website and work on SEO, design, and more. This can cost more than the initial investment and slow down your growth.
The tactics shared in the post can help reduce vulnerabilities to a great extent. So, follow the security measures described above and protect your business data.
Note: This blog article was written by a guest contributor for the purpose of offering a wider variety of content for our readers. The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of GlobalSign.







