Over the years, DevOps has been a collaborative culture which has grown in popularity, and evolved to incorporate security into the pipeline to reduce the number of security vulnerabilities. However, the shift to enable security in DevOps is not yet widely practiced. Whilst there may be a number of tools already in place within your organization to assist with integrating security into DevOps, they may no longer be fit for purpose and cause friction within development team. But within the DevSecOps toolchain, there are several instances where automated security and risk assessment tools can be implemented within the workflow to address gaps and supplement existing capabilities.
In this blog, we’ll take a look at the 10 phases you can consider when implementing security and risk assessment tools to reduce friction and improve speed and efficiency, with automation in mind.
The DevSecOps Toolchain: 10 Phases of Opportunity
Within the DevSecOps Toolchain, there are 10 phases of opportunity where you can consider where security fits into the pipeline and what potential security tools are required. Ultimately, the goal is to reduce security gaps whilst also embracing new technologies to decrease friction, and with automation, improve efficiency, speed and output.
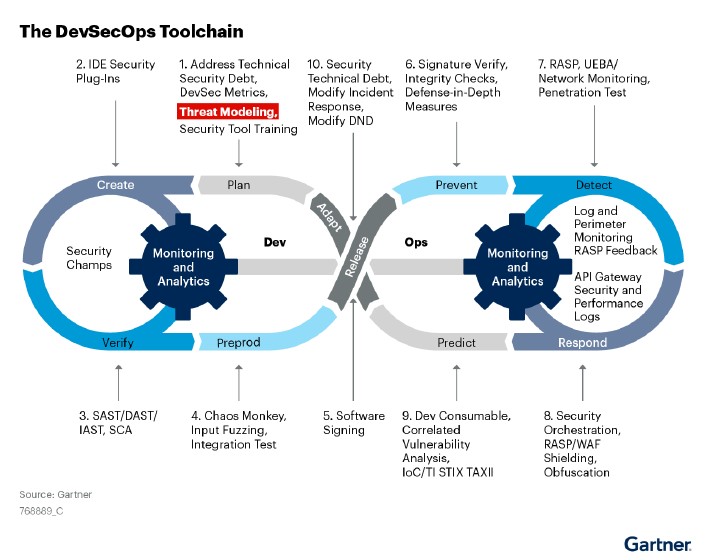
Source: Gartner® 3 Essential Steps to Enable Security in DevOps report
Click here for complimentary access to the full Gartner report
Phase 1: Plan
In the DevOps toolchain?, the ‘Plan’ phase sets the foundation for the development lifecycle. It’s here that goals, scope and requirements are defined and so naturally this is also the perfect opportunity to consider security and compliance requirements that should be fulfilled as well as any security training – tool-specific training especially.
Threat modeling should also be identified in this phase as it is easier to run a threat model from a known beginning than from scratch, but it will also give developers the opportunity to have a clean secure start in the upcoming pipeline.
By taking the time to integrate security requirements into the planning phase, key areas of concern both from a development and security perspective can be highlighted. This allow teams to make informed decisions that prioritize security from the outset, saving time and resources in the long run and reducing the risk of vulnerabilities entering the later stages of the DevOps pipeline.
Secure your DevOps pipeline with GlobalSign
Phase 2: Create
The creation phase focuses on developing and writing code that drives your applications and services. While speed and efficiency are paramount during this phase, it's crucial not to overlook security as vulnerabilities introduced here could lead to significant issues down the line. Therefore, it’s the prime opportunity to evaluate and, if necessary, implement security solutions that integrate directly with the CI/CD pipeline and work to mitigate those risks.
Automation security tools can come into play here by scanning code in real-time, identifying vulnerabilities, and provide instant feedback. This could include common security mistakes such as code injection, authentication issues, or data exposure. By utilizing the right tools, teams can rectify issues at the earliest stages of development.
Additionally, you can execute any further threat modeling and security architecture review with security coaches or security teams (for new components or larger projects that span multiple iterations) and open-source review.
Secure your code with GlobalSign
Phase 3: Verify
The verification phase is where we see the focus shift to ensuring that the code and configurations are not only functional but also secure. This is an opportunity for scanning known vulnerabilities and misconfigurations in known or reused code but also for unknown vulnerabilities in custom code.
Solutions which could be considered are:
- Software composition analysis (SCA) with governance capabilities can be used to enforce the organization’s open-source software (OSS) policy when components are downloaded
- Static Application Security Tools (SAST) and Dynamic Application Security Tools (DAST) can be utilized to test the product (or in the event of an attack), it will generate data that can be used to improve security or respond to the attack
- Mobile Application Security Testing (MAST) explores the potential security issues in mobile applications with quick analysis on client-side, server-side and third-parties.
By ensuring these principles are applied to development and delivery pipelines, this phase could be a pivotal chance to catch potential vulnerabilities early in the development cycle.
Phase 4: Preproduction
As we move into rigorous testing before deployment, preproduction is a vital point to consider security to ensure that vulnerabilities are identified and mitigated before reaching the production environment.
Evaluate application security testing solutions that identify how product code reacts to both known attacks and nondeterministic tests. A nondeterministic test may run for weeks and never find a vulnerability, or it may hit one on its first try. This reflects the nature of actual zero-day events. However, because DevOps emphasizes iterative development, the code runs through testing with greater frequency compared with waterfall methodologies.
Even though there is no specific recommendation to perform regular testing, this should be done consistently to keep up security posture. By implementing security automation tools here, teams can proactively address security concerns, reducing the likelihood of security incidents post-deployment.
Discover Automation with GlobalSign
Phase 5: Release
A critical phase in the workflow, the release phase is where the software or application transitions from development and testing environments into production. With all the phases so far, security has been paramount to see the reduction of vulnerabilities and this phase is no different to ensure that the release process doesn't inadvertently introduce new vulnerabilities.
One important security measure in the release phase is timestamping – by incorporating timestamping into the release process, organizations can maintain a clear and auditable record of every deployment, facilitating traceability and accountability. This can record every action and log with a precise time and date, making it easier to detect and respond to any anomalies or security breaches.
What’s more, timestamping can assist in keeping up with regulatory compliance, enabling organizations to demonstrate a comprehensive timeline of software releases and changes for auditing purposes. Timestamping is an ideal opportunity for an automation tool to make the process more efficient, reliable and reduce the margin for human error and overall enhance the security posture of the release phase, and ultimately the development cycle.
Secure your pipeline with timestamping
Phase 6: Prevent
The primary focus of this phase in the DevSecOps toolchain is to proactively defend against security threats and vulnerabilities before they can impact the system. The prevention phase emphasizes the importance of building strong security measures into the architecture by:
- Providing configuration assurance to confirm that code runs as expected and meets all requirements to be released into production
- Implementing application control and allow-listing to ensure the server workload is running appropriately
Phase 7: Detect
Not all vulnerabilities will be identified during development and some will, inevitably make it into production, and sometimes the fast-pace of the DevOps culture will create security blind spots. However, the detect phase can act as a crucial safeguard by continuously monitoring the environment for any signs of security vulnerabilities, breaches, or anomalies.
Security tools can play an indispensable role in providing real-time insights into the system's security posture including; tracking system logs, network traffic, and user activities. With automated alerts and notifications, this will enable teams to swiftly detect any irregularities and help them to respond promptly to emerging threats, reducing the time between detection and mitigation.
Phase 8: Respond
Despite the best preventive efforts, security incidents can occur. The respond phase is where organizations can equip themselves to address these incidents effectively and mitigate the potential damage and minimize downtime.
By leveraging security response technologies teams can, through the use of APIs, actively detect the type of attack that the application is experiencing, facilitate an appropriate defense, and alert or record the attack. Working in real-time, these tools can assist in providing a swift and consistent response through predefined actions. Any information discovered in this phase should be fed back into the plan phase on the next lifecycle to present a continuous and strong security posture, whilst minimizing any security technical debt.
Talk to us about our APIs integrations
Phase 9: Predict
In this phase of the toolchain, the focus shifts from reaction to proactively anticipating and mitigating threats. Work with teams to use the visibility and telemetry from the detect and respond phases to predict which countermeasures the system will need to improve security. Data from the attack surface must be collected, analyzed and fed back into the product planning cycle to support improved threat modeling. This will also help to enhance the understanding of security requirements for subsequent products. By predicting security issues before they manifest, DevOps teams can take preventive action and develop strategies to strengthen their defenses.
Phase 10: Adapt
Even with all the security tools throughout the past 9 phases, it’s inevitable that gaps and areas for improvement will be encountered. By utilizing all the information gathered across the phases in the tool chain, this will inform the next round of requirements. The adapt phase signifies the importance of staying flexible and responsive to the changing threat landscape. This is a prime time to reconfigure and refine applications to better support integrated security in products and DevSecOps team must continually review and evolve their tools and practices to ensure agility is not impacted.
Final Thoughts
Organizations can maintain a proactive security posture throughout the 10 phases of the DevOps toolchain to swiftly mitigate threats and ensure that workflows remain resilient and secure in the face of ongoing challenges. By embracing security and risk assessment tools, a strategic advantage can be obtained and enterprises can create a robust, resilient, and agile development and deployment process.
Throughout this blog we have shown how security can be weaved into the different stages of the DevOps pipeline and can help to bolster defenses, identify vulnerabilities, and expedite responses to potential threats. As the DevOps landscape continues to evolve, the fusion of security into the workflow is pivotal for maintaining the integrity and trustworthiness of your software. Embrace the power of automation security tools to safeguard your DevOps practices, foster innovation, and build a future-ready organization in an ever-evolving digital landscape.
Ultimately, embedding security into the toolchain is one step to enabling security in DevOps. To discover more steps you can take to enable security in your organization’s DevOps culture, you can click here for complimentary access to the Gartner® report: 3 Essential Steps to Enable Security in DevOps.
Get Started with Embedding Security into Your Toolchain
In this blog, we’ve outline 10 opportunities you could can consider implementing security within the DevOps Workflow but the reality is you can start at any time. GlobalSign can help you overcome security challenges and help you get started with certificate lifecycle management through REST APIs. If you want to talk to our team about your requirements, please get in touch.
Gartner, 3 Essential Steps to Enable Security in DevOps 1 March 2023, Daniel Betts Et Al.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.








