Editor’s Note: This post was originally published in May of 2018 and has been updated by GlobalSign Product Manager Cally Fritsch to provide new details about the browsers’ plan to end support of TLS 1.0 and 1.1 in March of 2020.
As we’ve explained in the past, SSL and TLS are cryptographic protocols that provide authentication and data encryption between different endpoints (e.g., a client connecting to a web server), with SSL the predecessor to TLS. Since SSL’s first iteration back in 1995, new versions of each protocol have been released to address vulnerabilities and support the strongest and most secure cipher suites and algorithms. We are currently on TLS 1.3, which was approved by the IETF (Internet Engineering Task Force) in March of 2018.
As a best practice, you should configure your servers to support the latest protocol versions to ensure you are using only the strongest algorithms and ciphers, but equally as important is to disable the older versions. Continuing to support old versions of the protocols can leave you vulnerable to downgrade attacks, where hackers force connections to your server to use older versions of the protocols that have known exploits. This can leave your encrypted connections (whether between a site visitor and your web server, machine to machine, etc.) open to man-in-the-middle and other types of attacks.
You might have also seen the recent news that the browsers are officially removing support for TLS versions 1.0 and 1.1. Just another reason to make the switch to TLS 1.2 or 1.3, if you haven't already. According to the Register:
"Apple said: 'Complete support will be removed from Safari in updates to Apple iOS and macOS beginning in March 2020.' Google has said it will remove support for TLS 1.0 and 1.1 in Chrome 81 (expected on March 17). Microsoft said it would do the same 'in the first half of 2020'."
Related: Need a refresher on the difference between SSL and TLS? Check out our explanation here.
What's Behind the Change?
Various vulnerabilities over the past few years (e.g., BEAST, POODLE, DROWN…we love a good acronym, don’t we?) have had industry experts recommending disabling all versions of SSL and TLS 1.0 for a while now. PCI Compliance was another driving factor. On June 30, 2018, the PCI Data Security Standard (DSS) required that all websites needed to be on TLS 1.1 or higher in order to comply.
Check If Your Site Supports SSL and TLS 1.0 Protocols
If you’re not sure which protocols your site supports, you can use our free SSL Server Test. Navigate to the Protocols section of the results page; you’ll see a list of all the protocols and whether or not you currently have them enabled. The below example is a “good” bad example of how your site should be configured, since it still supports SSL 2.0, SSL 3.0, and TLS 1.0 and doesn’t support TLS 1.2.
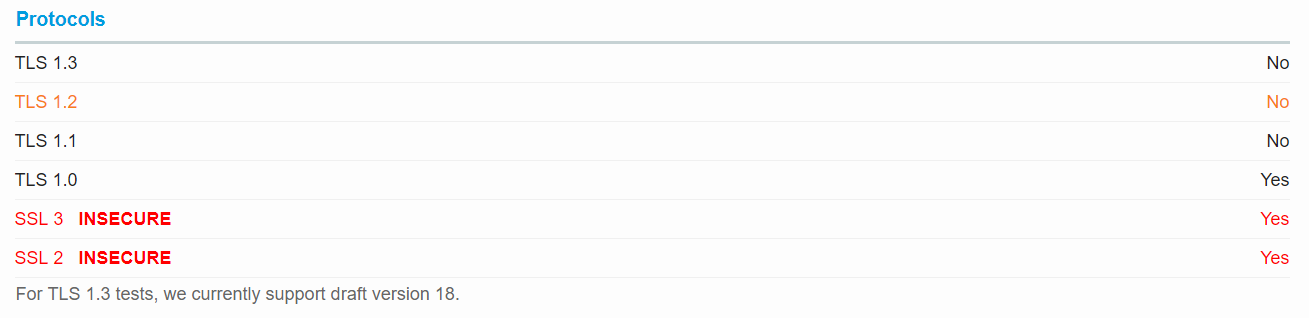
Example protocol support results form GlobalSign's SSL Server Test
You can find more information about what versions of servers and clients support each protocol, along with instructions for disabling the old protocols on our support site.
Reminder: Certificates Are Not Dependent on Protocols
In case you’re worrying about how you’re going to replace your certificates before the upcoming deadlines, we want to remind everyone that certificates are not dependent on protocols. Protocols are determined by your server configuration, not the certificates. So fear not, you don’t have to rip and replace your entire certificate inventory to accommodate this change!
In Summary
- Use our free server configuration test if you’re not sure which protocols you currently support
- You must disable support for SSLv2, SSLv3, and TLS 1.0 because they are outdated and vulnerable (and also to maintain PCI DSS compliance)
- You should disable TLS 1.1 if you can because there are known security vulnerabilities
- You should enable TLS 1.2 and 1.3
- Read our support article for instructions on how to change your server configuration and enable/disable the appropriate protocols
As for GlobalSign’s plans, we disabled SSL protocols a long time ago and ended support for TLS 1.0 and 1.1 for our web properties to ensure PCI DSS compliance. We will continue to support 1.2, and are working on support for 1.3 now.





