Code Signing Certi¬ficates are used by software developers to digitally sign applications, drivers, executables, and software programs for end-users. It is an operation where a software developer or distributor digitally signs the coded file sent to assure users that they are receiving the original software. The certifi¬cates verify that the signed software is legitimate and comes from a known software vendor, as it mentions all the required details related to the vendor along with the timestamping.
The Importance of Code Signing
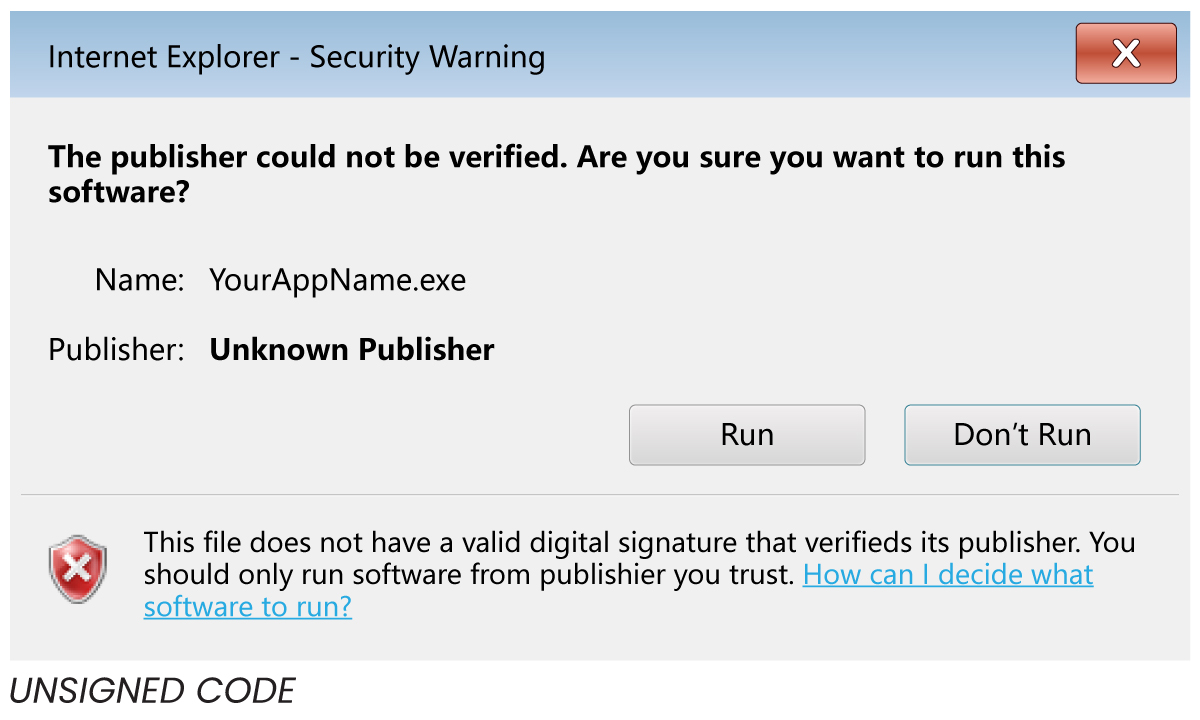
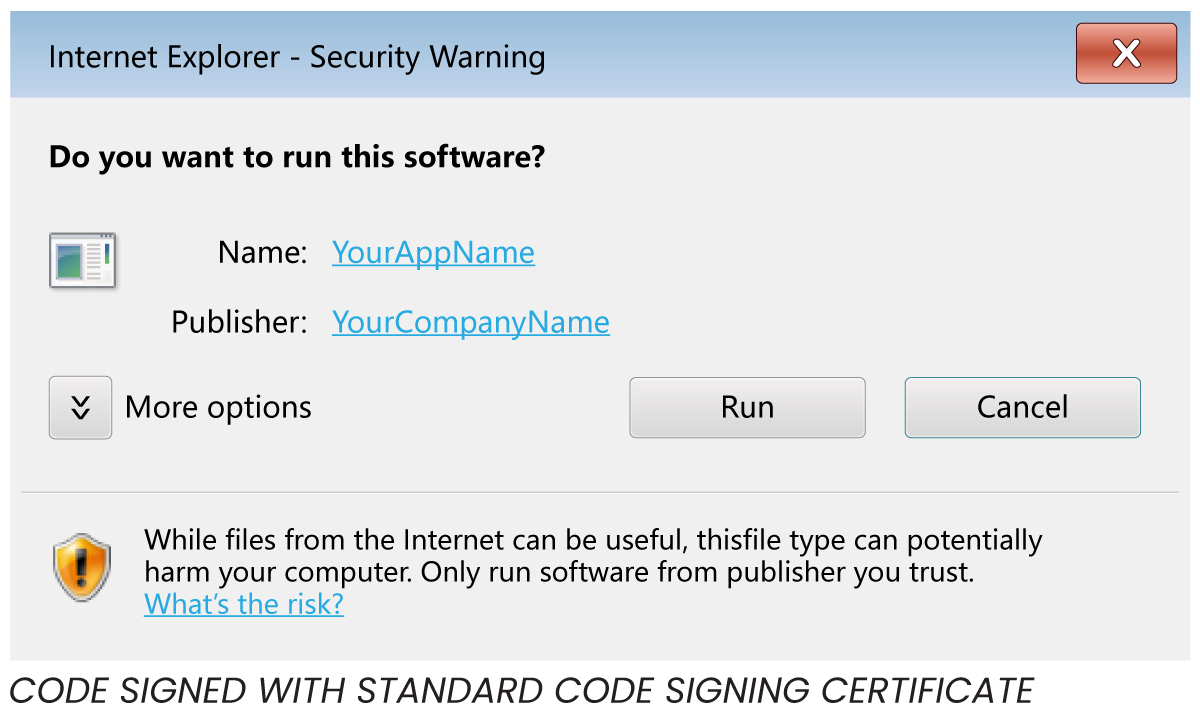
Today, as we can download any software from the internet, code signing has become crucial for software developers and distributors to help them protect their product. An attacker with enough experience can easily mask themselves as a legitimate user to plant malware on a victim’s computer. Code Signing Certificate assures these varieties of attacks cannot occur, as long as users only download software from a legitimate source and with a legal code signing certificate. In today’s time, when software is downloaded onto a computer, the OS verifies the digital certificate to assure the legitimacy of the software attempting to be installed. If no digital certificate is found, then the user gets an alert software and is prompted to either stop or continue the installation.
Types of Code Signing Certificates
- Standard Validation Certificates:
This is the default type of code signing certificate and involves basic validations of the publisher or developer by the CA. To get a standard code signing certificate, software publishers need to meet some basic requirements such as minimum key length, maximum validity period, and time stamping for digital signatures. - Extended Validation (EV) Certificates:
EV code signing certificates involve a high level of validations and vetting of the software publisher by the CA and are usually issued on a hardware token for additional levels of security. To get an EV certificate, apart from the basic requirements of standard certificates, software publishers also need to conform to much more stringent requirements – for example, maintaining private keys in a Hardware Security Module (HSM) that is compliant with FIPS (Federal Information Processing Standards) 140 Level-2 or equivalent.
| Standard Code Signing Certificates | Extended Validation (EV) Code Signing Certificates | |
|---|---|---|
| Certificate Features | ||
| Information displayed in Certificate | Organization Name | Organization Name, Address & Type |
| Removes "unknown publisher" security warnings | Yes | Yes |
| Signature does not expire when Time Stamping is applied | Time stamping available & recommended | Time stamping available & recommended |
| Sign an unlimited number of applications | Yes | Yes |
| Compatible with major platforms (Authenticode, Office VBA, Java, Adobe AIR. Mac OS, Mozilla) | Yes | Yes |
| Key storage options | Cryptographic USB token HSM Other hardware storage token:SD Card or USB token Azure Key Vault |
Cryptographic USB token HSM Azure Key Vault |
How Code Signing Works
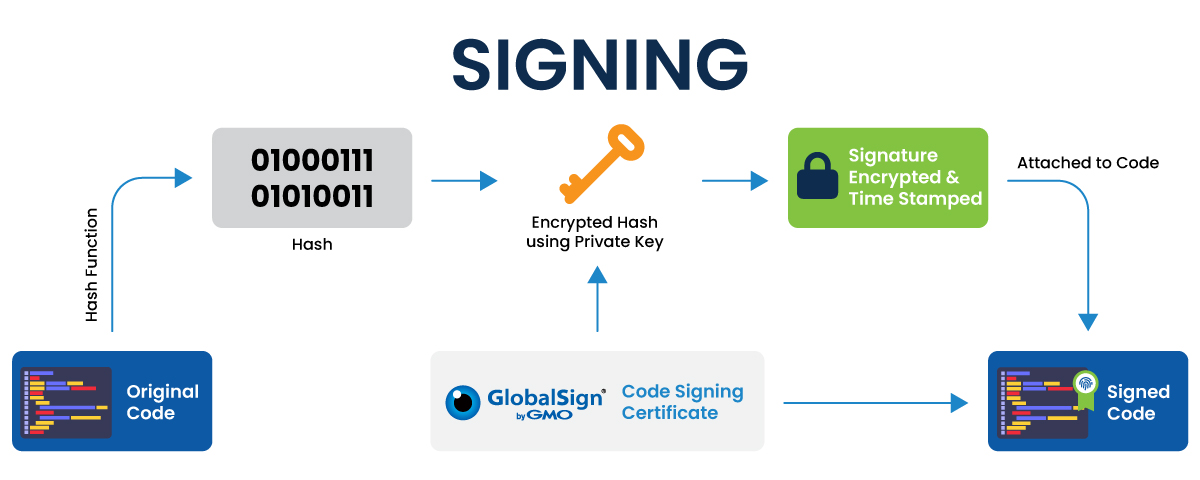
Code signing follows several steps. It starts with the creation of a unique key pair. The key pair created is a public-private key pair since code signing uses public key cryptography. Once the key pair is made, the public key is shared with a trusted certificate authority, confirming that the key belongs to the owner by returning digitally signed code signing certificate. A Certificate Authority is a highly trusted entity accountable for signing and generating digital certificates.
Once the public key and a digital code signing certificate are verified and returned, the code of the software is run via a hash function. A hash function is a one-way process that pivots the text added into the function and then into an arbitrary mixture of values that cannot be changed. This provides a value for comparing the data sent to the consumer. The output, or digest, is then encrypted using the private key. The private key is used for encryption instead of the public key because the developer would need anyone to read the message but no one to tamper with it. The digest, hash function, and code signing certificate are now integrated into a signature block and positioned into the software, which is sent to the user.
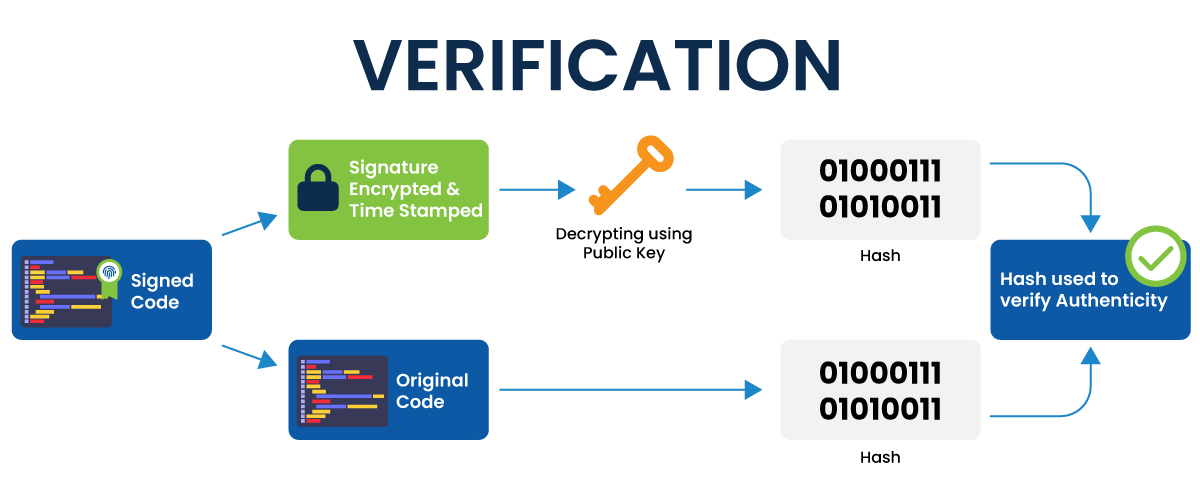
Finally, when the software is downloaded to the user's computer, the system inspects the authenticity of the code signing certificate. Once the authenticity is ensured, the digest is decrypted using the initially created public key. The hash function is now used on the software’s code, and the resulting digest is compared to the digest sent by the developer. If the digests match after comparison, the software is safe to install; otherwise, it shows a pop-up that the software is not secure.
Advantages of Code Signing
Code signing provides many benefits, the main ones listed below:
- Authenticity:
Users can trust the software they are downloading if it has a code signing certificate. They need not fret about downloading malware onto their computer system. The Code Signing Certificate helps in authentication, which acts as a two-way street, as it promotes trust on both sides of the exchange. The user can trust the sender, and even the developer can trust that their software got to the valid location and is not being misused. - Integration:
Since many of the biggest trusted mobile and web application stores, such as the IOS AppStore or Google’s Play Store, require code signing, developers can distribute their software through even more platforms. - Timestamping:
Time stamping is an optional part of the code signing process, which allows software to recognize whether an applied code signing signature is valid–even after a code signing certificate expires. Without time stamping, expiration/revocation of code signing certificates would lessen the confidence of customers in the same software product. Timestamps make sure that even if certificates lose their validity or are revoked for some reason, their signatures remain valid, secure, and trusted.
Weaknesses of Code Signing
There are several weaknesses to code signing, as well, including:
- Protection of Keys:
Inappropriate security of the private key can result in the insecurity of the software. If a legitimate private key is stolen, the hackers can encode their malicious software with the private key, notifying the user that the software is safe to use, even if it isn’t. - Ignorance:
If the user allows the software installation, even if the Operating System displays it is not legitimate, then code signing is rendered useless.
Conclusion
Unsigned software is subject to tampering, such as the insertion of spyware or malware, so end users are encouraged not to run unsigned code. Downloading or running unsigned applications will generate worrying “Unknown Publisher” security warnings. Once digitally signed, customers can be sure of the identity of the software developer and that the software has not been altered since being published by the original vendor. The security warnings that appear with unsigned code are replaced with notifications containing the software publisher’s information – adding a basic level of trust to the application.
GlobalSign Code Signing Certificates provide you with the ability to attest to the authentication, security, and integrity of your code along with that our certificates are multi-purpose that can be used to digitally sign:
- Microsoft Authenticode files (32 and 64bit) including Kernel software
- Adobe Air Applications
- Apple Desktop Applications
- Java applications
- Microsoft Office Macros and Visual Basic
- Mozilla XPI packages for Firefox
For more information, please contact us today.






