KEY POINTS EXPLAINED
- What is a Public Key Infrastructure (PKI)?
- Top 3 Benefits of PKI
- Conclusion
I think you will agree when I say:
With the progressive evolution of the internet, ensuring the security of businesses' online presence has become an increasingly formidable task, owing to the relentless advancements in cyber threats.
While the battle against cyber threats remains ongoing, the risk can be significantly mitigated by incorporating Public Key Infrastructure (PKI) into your business strategy.
Now before we dive deeper, let us try to understand the meaning of a Public Key Infrastructure (PKI)?
What is Public Key Infrastructure (PKI)?
Public Key Infrastructure (PKI) serves as an integral foundation for establishing trust, enabling secure transactions, and safeguarding sensitive data in the digital realm. Using the cryptographic techniques, PKI establishes a framework for managing the generation and verification of digital certificates and encryption keys that ensures the authenticity and confidentiality of information exchanged between parties.
Before we move forward, let us look at some concerning cybercrime numbers as of March 2022-
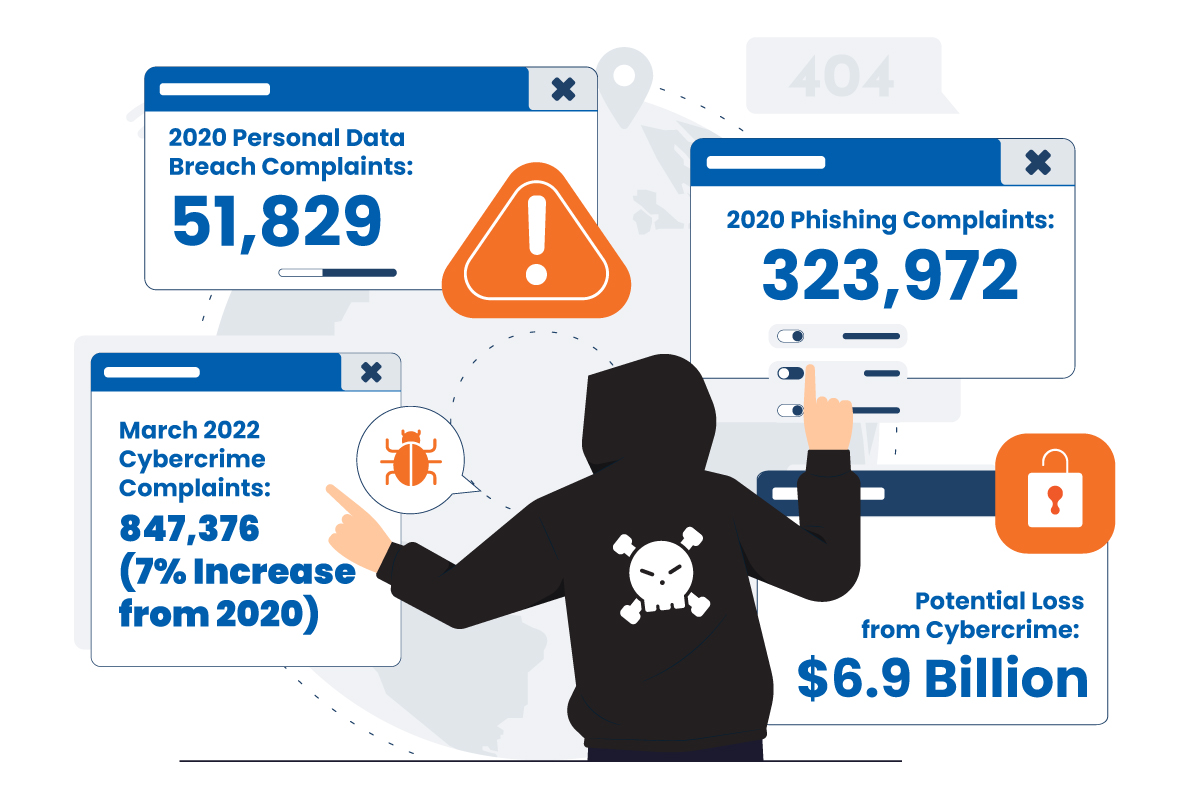
- Internet Crime Complaint Center (IC3) received 847,376 cybercrime complaints, with a concerning 7% increase compared to the previous year.
- Approximately 51,829 complaints were related to compromised personal data.
- A staggering 323,972 complaints were related to phishing scams.
- Total potential loss attributed to these incidents amounted to $6.9 billion.
These staggering numbers underscore the critical significance of establishing a robust PKI ecosystem to safeguard against potential malicious threats effectively.
Top 3 Benefits of PKI
- Secure Email Communication
One of the uses is securing email communication. By implementing PKI, companies can encrypt their emails and ensure that only authorized recipients can decrypt and read them. This is achieved by issuing digital certificates to employees that are used to encrypt and decrypt email communications.
To ensure the security of PKI-based secure email communication, companies should:- Establish a robust certificate management system to deal with the issuance, renewal, and revocation of certificates.
- Implement strong authentication mechanisms to prevent unauthorized access to employees' email accounts.
- Regularly update and patch email servers and related software to mitigate potential vulnerabilities.
- Document and Code Signing
PKI enables companies to digitally sign important documents, such as contracts and legal agreements, and software code to ensure their integrity and authenticity.
Digital signatures are unique to the signer and provide convincing evidence of the document or code's origin and unchanged content.
To ensure the security of PKI-based document and code signing, companies should:- Protect their private signing keys from unauthorized access and regularly audit access logs.
- Implement software and processes to verify the validity and integrity of digital signatures.
- Periodically review and update cryptographic algorithms and key sizes to stay ahead of potential vulnerabilities.
- Secure Remote Access
In today's business landscape, large corporations frequently operate with a distributed workforce, requiring the establishment of secure remote access to their internal networks and valuable resources.
PKI can be used to establish secure virtual private network (VPN) connections, enabling employees to access company resources securely from remote locations.
To ensure the security of PKI-based secure remote access, companies should:- Implement two-factor authentication to prevent unauthorized access.
- Use strong encryption algorithms to protect the confidentiality of data transmitted through the VPN.
Regularly update VPN software and firmware to address any known vulnerabilities.
Conclusion
While PKI's primary use in big companies is well-known, there are several surprising applications that contribute to secure communication, authentication, and data protection. However, to ensure the security of these uses, companies should establish robust certificate management systems, implement strong authentication mechanisms, regularly update software and hardware, and stay vigilant against potential vulnerabilities.
To summarize, PKI is at the core of GlobalSign's offerings, enabling the issuance of digital certificates, secure communications, authentication, and data integrity, contributing to a safer and more trustworthy digital landscape for individuals and businesses alike.
Are you looking for a PKI solution that works for your business? Look no further! Contact us and we will reach out to you.






