Ready to automate? Trial ACME today!
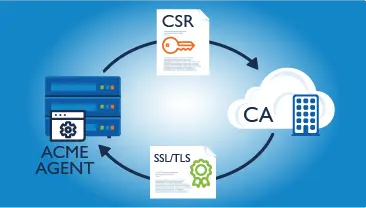
GlobalSign's ACME integration can help you automate your certificate management. Talk to us to optimize your certificate infrastructure.
- Reduce costs by eliminating the need for internal PKI expertise, ongoing maintenance, and associated costs
- Increase volume and velocity of certificate issuance and renewal with almost immediate provisioning
- Eliminate the need to manage PKI in-house or rely on self-signed certificates with a flexible, scalable and publicly trusted solution