What is ACME SSL?
Let’s say your organization has taken the first step towards cybersecurity by using multiple digital certificates. However, due to the lack of certificate management knowledge, the certificates have expired. Outages, downtimes, and breaches that resulted in sensitive data leakage have occurred. This sets the importance for proper certificate management.
Organizations often consider certificate management a complicated process. With manual management systems requiring intensive manpower, tracking certificates can be challenging. For this reason, ACME was designed.
The Automated Certificate Management Environment (ACME) protocol automates certificate lifecycle management for SSL/TLS and provides a framework for clients to communicate directly with the CA to manage the SSL/TLS certificate lifecycle – from issuance, installation, revocation, and replacement.
ACME History
ACME was created by the non-profit corporation Internet Security Research Group (ISRG) for Let’s Encrypt and is backed by the Electronic Frontier Foundation. ACME made it possible to automatically renew and replace certificates without any action needed from the website owners. In March 2019, the ACME protocol was published as an internet standard and has since gained support among PKI vendors, CAs, and browsers supporting various X.509 certificates.
Benefits of ACME SSL
Various benefits are brought by automation through ACME SSL. With its main objective to make certificate lifecycle management more efficient, ACME:
- Saves time and resources for your organization by eliminating manual tasks such as filling out CSRs and manually completing domain validations.
- Eliminates human errors in management of SSL/TLS certificates, avoiding outages.
- Allows quick issue mitigation through replacement of old certificates in the case of compromise.
- Enhances security through its open-source feature.
Google's 90 Day Certificate Validity Plans Require CLM Automation
Extracted from our recent blog:
Following the CA/B Forum face-to-face meetings held in early March 2023, Google announced its intention to reduce maximum certificate validity to just 90 days for all publicly-trusted SSL/TLS certificates. While there is not yet an effective date or deadline for this change – now is the time to begin planning automation of your certificate lifecycle management for SSL/TLS.
To eliminate the burden of having to manage certificates manually, ACME can be utilized to fully automate certificate management and streamline your organization’s SSL/TLS issuance, installation, revocation, and replacement.
GlobalSign ACME
ACME is generally free. However, using these free services requires ACME users to go through crowd-sourced support in forums, which operate without SLAs. This makes it challenging to find the best solution for your organization.
GlobalSign’s ACME service changes this. Aside from receiving full support and SLAs from a trusted Certificate Authority (CA), this ACME service is powered by Atlas, GlobalSign’s next-generation Cloud CA that features high throughput and availability. Customers also have the flexibility to use any ACME client based on the organization’s needs. With over 25 years of industry experience, GlobalSign ensures that your business is protected by a trusted CA – your partner in finding the right solutions.
GlobalSign’s ACME service can issue both domain and organisation validated (OV) SSL/TLS certificates
GlobalSign is constantly looking to improve the certificate management. Recently, GlobalSign announces ACME OV certificate support. GlobalSign’s ACME OV certificates are issued from its high-volume cloud-based certificate management platform to avoid any delay within the certificate lifecycle. GlobalSign’s ACME OV certificates are ideal for a wide range of organizations seeking a high level of support – and affordable pricing – from one of the world’s most trusted and relied upon Certificate Authorities.
ACME SSL in APAC
There are over a hundred Certificate Authorities in the market valued at USD 127 million in 2021. Asia Pacific is one of the fastest growing markets for CAs, attributed to the increasing instances of cyberattacks, tightening regulations, and the IoT trend in the region. Despite the potential growth, not all certificate authorities offer ACME, and awareness for cybersecurity products like automated certificate lifecycle management remains a challenge due to the complications in its open-source structure. GlobalSign eliminates this issue. Being one of the few providers of ACME in the APAC market, GlobalSign continues to raise awareness about the benefits of ACME. Moreover, GlobalSign’s ACME boasts 24/7 support and operates through SLAs, ensuring that the needs of the organization are being met.
How to use ACME
Automating certificate management is made possible through ACME by installing an open-source agent and authorizing it to carry out operations such as CSR generation, domain ownership verification, and certificate installation and revocation. Standard processes in configuring ACME involves agent selection, CA selection, authorization, challenge issuance, signing, and setup completion. The main idea in using ACME is establishing communications between the client and the server, with a verification done through key pairs.
How do I set up ACME?
In GlobalSign’s integration with ACME, customers set up an account on the GlobalSign Atlas platform and validate their organization information. You will need to link the ACME client with your Atlas account using ACME External Account Binding (EAB). Once EAB is completed, ACME is used to automatically request and revoke CA/Browser Forum compliant SSL/TLS certificates from Atlas without having to interface with the Atlas portal or APIs.
Visit our repository to learn the step-by-step Atlas onboarding process.
Does using ACME mean I only need to validate my profile once?
To ensure that the SSL certificate remain valid and secure, CAs routinely conduct a validation process each time a certificate is renewed. This is an important process to confirm that the domain name for which the certificate was issued remain valid and still under your control and have not been transferred to someone else. It also confirms that you have full control and authority to request a renewal of the certificate. While ACME is a critical solution to automate, simplify, and strengthen your organization’s certificate management, security measures such as validation process must still be routinely conducted each time a certificate is renewed.
SSL certificate automation through ACME
ACME is a lightweight, convenient way to manage the SSL/TLS lifecycle. Certificate actions, from issuance, renewal, to revocation, can be completed without human intervention. This makes the certificate lifecycle management process more efficient and accurate. To further understand this, let’s discuss how the ACME protocol works.
ACME protocol
Certificate management automation is made possible through the ACME protocol. The ACME protocol’s main purpose is to provide a way to validate that someone who requests a certificate management action is authorized. The verification process uses key pairs. The agent generates and shares a key pair with the Certificate Authority. When validated, the agent uses the key to digitally sign the CSR that is sent to the CA through HTTPS. This CSR, along with the public key, is used to issue the certificate and sent back to the agent.
It is important to note that the agents can be automated, and the process does not require any human intervention, minimizing errors in filling out CSRs.
How does GlobalSign’s ACME protocol work?
One of the best features of GlobalSign’s ACME is the flexibility it provides. The ACME client is chosen based on organization’s needs, while the agents are stored on the web servers. The agents are configured to contact Atlas and an account key pair is created. After which, the following will occur:
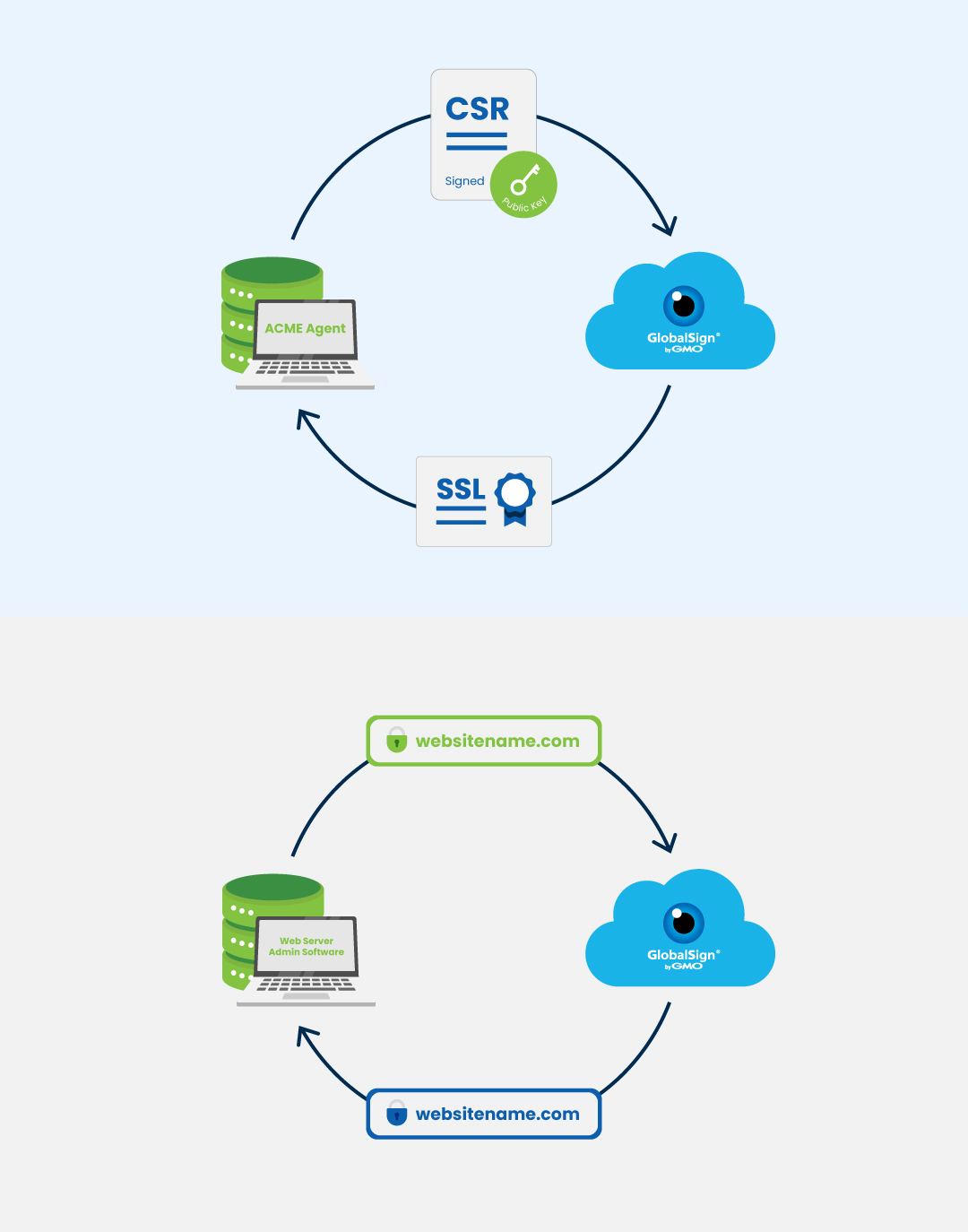
- The agent sends a request and digitally signs it with its account key pair.
- Atlas, GlobalSign’s cloud CA, sends a domain validation challenge to verify the agent is authorized to act on behalf of the server. The agent sends a response and signs it with the account key pair. Verification is done by Atlas.
- After successful verification, the agent generates a CSR and sends it to Atlas with a digital signature and the account key pair.
- Atlas verifies the digital signature and GlobalSign issues the SSL/TLS certificates.
- The agent receives the certificate and is installed to the web server.
How do I revoke SSL certs with ACME?
Certificate revocation works through sending a revocation request and signing it with the account key or private key of the TLS certificate for revocation. Atlas then verifies the digital signature, and the certificate is revoked by GlobalSign.
What are ACME clients?
An ACME client is one of the two entities in the ACME protocol. It is any software that can talk to ACME-enabled CAs to request certificate management actions or do integrations into other services. This runs on the user’s server or device, requiring a trusted SSL/TLS certificate.
ACME client implementations
Since ACME is open-source, ACME clients are offered by third parties. Multiple options are available for ACME client implementations. Listed below are the most common:
- Certbot – the Certbot client can help you issue or renew and install certificates. Certbot offers great documentation and works on multiple systems.
- Posh-ACME – Posh-ACME is a PowerShell module and ACME client designed to obtain SSL/TLS certificates from an ACME capable CA. However, it does not deploy certificates to the web server.
- GetSSL – GetSSL runs on virtually all Unix machines. This ACME client runs as a daily cron, automatically renewing certificates when required. Automatic updates are also supported to fix the script when bug fixes are required.
Other ACME client options include ACMESharp, Caddy, Sewer, and more. ACME Clients can be chosen depending on the need of your business.
ACME automation
The ACME protocol automates certificate lifecycle management communications between the CA and the organization’s servers. This happens through the communication between client and server, where the client uses ACME protocol to request actions like issuance, renewal, or revocation. This removes the process of filling out CSRs, a time-consuming task in manual certificate management. Once the client is verified, ACME servers respond to the request and executes the necessary action.
Automations through the ACME protocol eliminates other processes like server-to-server certificate installation, tracking certificate renewal through spreadsheets, and possible outages caused by expirations.
ACME server
While the ACME client runs on the user’s device, ACME servers run at CAs. The ACME server responds to the requests made by the client, executing the requests once the client is authorized and authenticated.
ACME Windows server
The ACME protocol may be more widely used in Linux servers yet automating certificates in Windows ecosystems is also possible. The process begins with choosing the right client. However, in most cases, the client cannot complete the installation process due to the inability to deploy the new certificate in Windows.
Common ACME clients’ options for Windows servers include Crypt::LE (previously ZeroSSL project), Certes, Posh-ACME, Certify The Web (Windows), and WinCertes Windows client.
ACME Nginx server
ACME can also automate certificate management in Nginx systems. In using ACME Nginx server, lua-resty-auto-ssl, Nginx ACME, and lua-resty-acme are commonly used.
Setting up in Nginx servers requires configuration by setting a location directive in Nginx’s config. After this, we can generate the certificates for both the root domain and the subdomain, using the site directory. To fully implement the ACME protocol, the certificate generated must be known to Nginx.
ACME Apache server
Version 2.4.30 and later versions of Apache supports ACME integration with various Certificate Authorities using the mod_md module for automated certificate management within the Apache ecosystem. This module generates and renews certificates via ACME protocol, avoiding downtimes caused by expirations. It also adds support for CAs through External Account Binding (EAB) when EAB values are required for ACME account registration with their respective ACME servers.
Who can provide ACME protocol?
SSL/TLS certificate lifecycle management does not have to be challenging. ACME offers a seamless experience through automation of manual processes. Moreover, GlobalSign’s ACME is the best solution in certificate management as it is powered by Atlas, ensuring that the ACME client serves the organization’s needs and is fully supported by a trusted certificate authority 24/7.
In the journey of your business towards cybersecurity, don’t let improper certificate management get in the way. GlobalSign’s ACME is available in the US, Europe, Canada, and now, Asia Pacific! Begin your automation journey by shooting us a message today. Let us know how we can help!







