When the date and time of an event is recorded, we say that it is timestamped. A digital camera will record the time and date of a photo being taken, a computer will record the time and date of a document being saved and edited. A social media post may have date and time recorded. These are all examples of a timestamp.
Timestamps are important for keeping records of when information is being exchanged or created or deleted online. In many cases, these records are simply useful for us to know about. But in some cases, a timestamp is more valuable.
Imagine this scenario: your organization electronically signs a legal agreement or NDA with another organization or contractor. Later down the line, it is discovered that the contractor has leaked information about the project under which the NDA was signed. The contractor disputes the NDA, arguing that information was shared prior to the signing of the NDA. Knowing when that document was actually signed is essential here.
In a legal setting like this, it’s not enough to just have a timestamp. If your argument comes down to when the NDA was signed, you need to be able to prove that the timestamp of the signature is valid, that it says the document was signed when it was actually signed. Timestamps that rely on system clocks are not enough, since it’s not difficult to alter the date and time locally on a machine. Plus, there are a variety of tools online that will allow you to change the modified, created and last accessed date of a document or PDF. So, how do we know if we can trust the timestamp?
What is a Trusted Timestamp?
This is where ‘trusted’ timestamping comes in. These types of timestamps are generated by a trusted third party using secure FIPS-compliant hardware, so they are not subject to manipulation by a local user. Trusted timestamping means that you can say with a high level of certainty that the date on the timestamp is accurate and hasn’t been tampered with.
RFC 3161 outlines the requirements a third party must meet in order to operate as a Timestamping Authority (TSA).
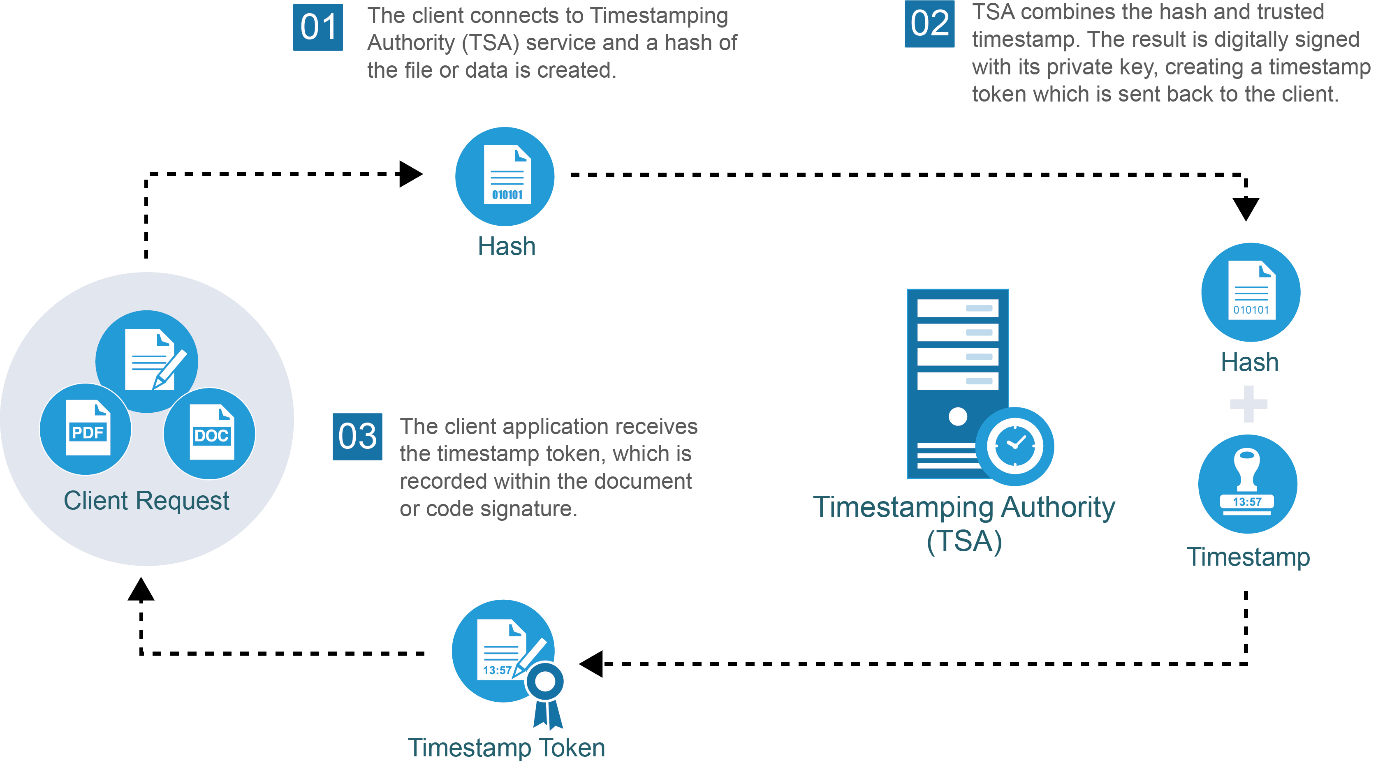
How Does Timestamping Work?
TSAs use Public Key Infrastructure (PKI) technology to apply timestamps. Here is a high level summary of the steps involved.
- The client application creates a hashed value (as a unique identifier of the data or file that needs to be timestamped) and sends it to the TSA.
- From now on, any change (even by a single bit of information) in the original file will require communication of changes with the TSA server.
- The TSA combines the hash and other information, including the authoritative time. The result is digitally signed with the TSA’s private key, creating a timestamp token which is sent back to the client. The timestamp token contains the information the client application will need to verify the timestamp later.
- The timestamp token is received by the client application and recorded within the document or code signature.
When the resulting timestamped data or file is opened in the future, the client application will use the TSA’s public key to authenticate the TSA (i.e. validate that the timestamp came from a trusted TSA) and re-calculate a hash of the original data. This new hash is compared to the originally created hash (step 1 above). If any changes have been made to the data since the timestamp was applied, this hash check will fail and warning messages will be shown saying that the data has been altered and it should not be trusted.
What Type of Transactions Are Timestamps Most Commonly Used For?
Trusted Timestamps add extra security to electronic signatures, digital signatures and code.
Electronically Signing Documents
Electronic signatures are quickly being adopted globally and across various industries; however, for an electronic signature to have the same legally binding value of a wet ink signature, it must satisfy the requirements of the law including compliance and auditability requirements.
Recipients of documents can verify when the document was electronically signed, as well as verify that the document was not altered after the date the timestamp vouches for. By using timestamping, organizations can protect their intellectual property and use the timestamps as strong legal auditable evidence.
Digitally Signing Documents
There are two main reasons for including a trusted timestamp when you digitally sign a document – ensuring Long-Term Validation (LTV) of the signature and adding non-repudiation or confidence around when the signature was actually applied.
Note: Part of the digital signature verification process involves a content integrity check, so while a timestamp also offers that benefit (knowing the document hasn’t been changed since the signature was applied), it’s not a major driver as it is with electronic signatures.
Long-Term Validation (LTV)
LTV means you can confirm that the signature was valid at the time it was applied, regardless of the status of the certificate at the current moment (i.e. if it’s expired or has been revoked). For example, if I sign a document today with a valid certificate and a trusted timestamp, but then my certificate is revoked or expires in two months, my signed document should still be valid any time after that.
Depending on the program you use to apply the signature, you may need to include a trusted timestamp with your signature in order to achieve LTV. In those cases, the timestamp is used as a reference point for checking validity of the signature. If the program sees the current certificate status is revoked or expired, but the signature was applied before revocation or expiration, it will show the signature as still valid. Most programs require a trusted, third party timestamp for this; using your computer’s system clock is not reliable since it can be manipulated.
Microsoft Office programs and Adobe Versions 6, 7 and 8 require a timestamp for LTV. Adobe 9+ embeds revocation information (CRL or OCSP) at the time of signing, which achieves the same goal of verifying validity of the certificate when the signature is applied, so a timestamp is not needed for LTV.
Adding Confidence around Date and Time the Document Was Signed
As the example from earlier in the post highlighted, sometimes you need to know, with a high degree of confidence, when a document was actually signed. This is especially critical for scenarios involving time-sensitive transactions and audit trails.
Trusted timestamps support these scenarios because they are applied using independently verified and auditable date and UTC (Coordinated Universal Time) sources. This means they are not subject to tampering like a local system clock is, so you know with certainty when a signature was applied.
Digitally Signing Code
As mentioned above, digital signatures need LTV in order to stay valid despite a future status change (e.g. expiration or revocation). For signing code, this is achieved by adding a trusted timestamp.
Without a timestamp, signatures will expire or invalidate when the certificate expires or is revoked and end users will see scary warning messages that they should not trust the code. With a timestamp (and LTV), the signature will still be trusted since the signing certificate was valid when the signature was applied.
What Next?
If you are looking to implement trusted timestamps in your organization, visit our website to find out more.







