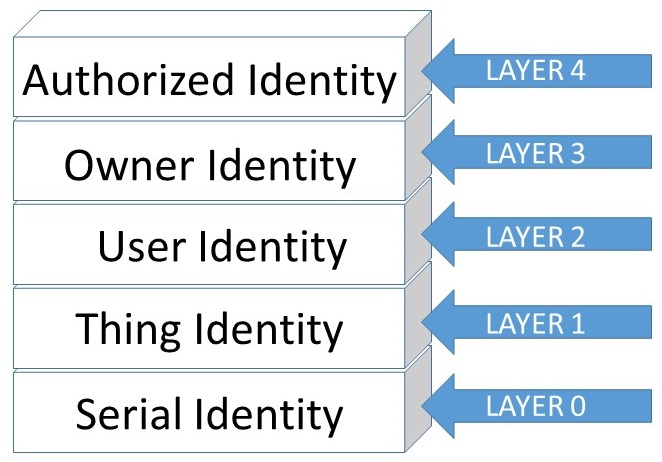
When we access networked data, it travels through several layers from the physical cable all the way to the application. Could this same type of layer model work for Identity as well?
Layer0: The "Serial"
Connected devices have an identity. In most cases, it's a serial. Each manufacturer will assign a unique string of characters to a device on the assembly line. Serial number in itself does not give any protection or security features. It just identifies the device. It cannot be changed. Serial numbers are not exclusively for devices. Quite a few other things have serial numbers, such as identity documents and your $100 bill.
Layer1: Thing Identity
All of the “things” that have processing power could be embedded with a credential, or identity. This identity would utilize the Layer0 information as part of the identity. A certificate issued to a connected device including the serial number would give the device a true identity. The processing power within the device then allows operations to be made using this identity. The device could use the identity to properly authenticate itself to an outside resource. Every day, we use these types of identities or benefit from their existence. Each time you see the green box in your browser’s address bar you are interacting with a “thing” (in this case an online service) that has been issued an identity. It's not using a serial number, but a web address that has been vetted by a Certificate Authority.
Layer2: User Identity
We use the “things” every day. In many cases, these “things” want to make sure who is using them. The basic user identity can be used to authenticate a user to a “thing.” We all have many user identities scattered across different services. Most of our identities are weak password based or social identities, but we do have stronger identities as well such as online banking identities and government issued eIDs. From the identity perspective, this would still be one layer with multiple levels of strength.
Layer3: Owner Identity
The “things” always have an owner. Each device, service and according to ITIL, a process, should have an owner. The owner is capable of deciding who should be allowed to do what with the “thing.” From the technical perspective, the Owner Identity does not differ from the User Identity as it can also be based on anything between the password and a PKI smart card. From the identity perspective, it could be reasonable to separate these layers as the owner identity has the decision making power for the “thing.”
Layer4: Authorized Identity
Authorization can give special powers to identities below. Authorized Identity has a specific privilege to conduct an action with the Thing. The authorization is given by the Owner Identity. Authorization in itself is a complex issue, and can be based on a variety of technical aspects, but from the identity perspective the receivers are the layers below.
All of these identity layers and their billions of “things” can be intertwined forming a huge mesh of connections. Identity and Access Management (IAM) is a technology that tries to bring order into this. IAM also tries to minimize the number of required identities. In an ideal situation, each instance of a “thing,” including users, would have a single identity and the relationships would be described in the Layer4: Authorized Identities. Another part of the IAM is that a “thing” can require that a process or user accessing it has a strong enough identity. The access management part of the IAM can be used to centrally manage these requirements.
If you are lost in the world of Things and Identities, look for an IAM solution to help you make sense of it. Check out GlobalSign’s comprehensive IAM solution today.