Control your chain of trust without managing PKI in-house
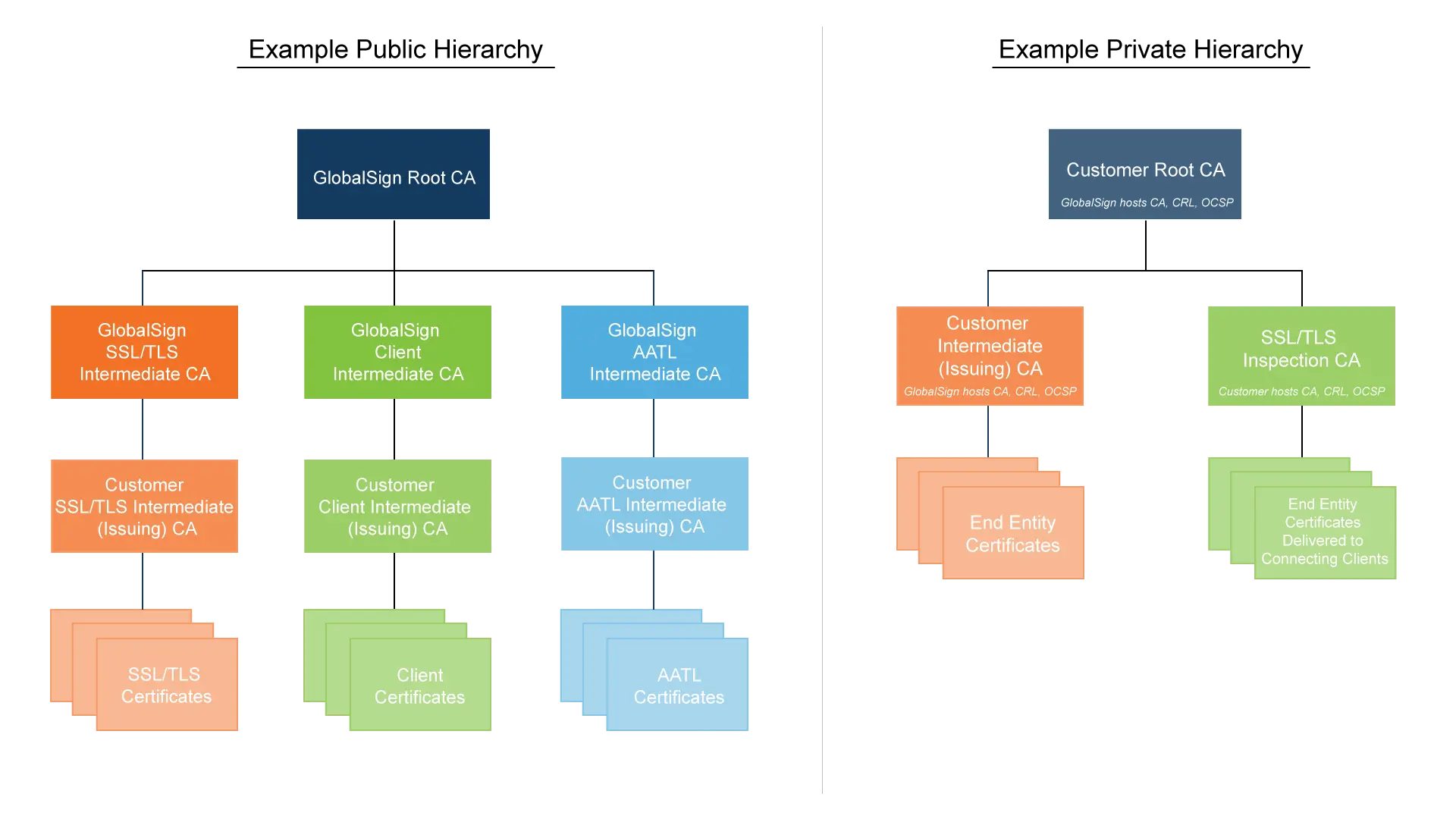
Dedicated intermediate CAs (ICAs), sometimes referred to as subordinate or issuing CAs, are used to issue end-entity certificates exclusively for one specific company. Having your own ICA or hierarchy gives you greater control over the chain of trust in your ecosystem, allowing you to only trust certificates issued from your trust model.
These CA hierarchies can be public or private trust and are branded to the customer, but they are hosted and managed by GlobalSign in our Web-Trust audited, secure data centers. Relying on GlobalSign to host your ICAs and roots ensures all CA components are properly protected and configured in line with the latest industry best practices - eliminating the cost and resource burden on internal teams to manage PKI. Note: In some rare cases (e.g., SSL inspection/decryption), the intermediate is hosted by the customer.
How It Works
GlobalSign supports both public trust customer-specific ICAs and private trust customer-specific hierarchies. Below are very simple examples of the many configurations we can support. With the exception of a few scenarios, all roots and ICAs are hosted and maintained by GlobalSign.